Continuous Authorization, or cATO, can mean different things depending on context. In the federal public sector, I’ve encountered numerous strategies and interpretations.
Human-Driven Assessments: The Traditional Approach
Traditionally, authorization assessments have been human-driven. We’ve explored continuous approaches, which typically involves increasing the frequency of assessments while reducing the number of controls evaluated. For instance, instead of triennial assessments covering all controls, we might shift to annual assessments focusing on one-third of the controls. Some organizations have progressed even further to quarterly assessments with a smaller subset of controls. In any of these cases, human-driven assessments remain the foundation of our compliance strategies.
Machine-Driven Assessments: The Innovative Frontier
On the other hand, we can enhance trust and efficiency through machine-driven tests. We can raise trust with machine-driven tests by delegating responsibility and pre-authorizing these tests for continuous monitoring. An example of this is the Air Force’s Party Bus, a project from Platform One that already holds an Authority to Operate (ATO). With machine-driven tests, human involvement can be limited to overseeing controls not monitored by machines. This hybrid approach leverages automation to support, but not completely replace, human assessments with machine-driven assessments.
Challenges in Implementing Machine Assessments
Machine tests have been around for a while, but the transition to machine-driven assessments is not without its challenges. It requires a careful evaluation of each machine test’s effectiveness and its ability to build confidence for any given control(s). Each test must be carefully mapped to specific controls and assessed for its risk mitigation potential. Although individual tests are beneficial, it is the aggregate results of these machine tests that solidifies trust for any given control. Additionally, without an agreed method to communicate test results, we’ve struggled to integrate machine tests into our compliance regimes.
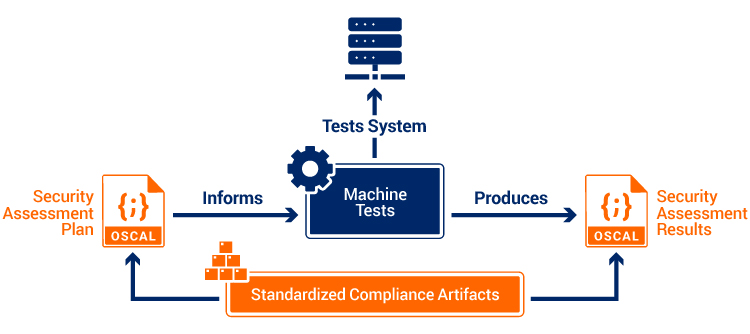
OSCAL: Bridging the Gap
Fortunately, NIST OSCAL (Open Security Controls Assessment Language) provides a valuable framework to support continuous authorization. Assessment Plans (APs), for instance, guide assessors in both human and machine-driven contexts. An OSCAL AP provides clear tasks and instructions for machines conducting assessments, enabling standardized and automated testing procedures. With OSCAL, machine assessments can produce standardized Assessment Results (AR) documents, which can then be integrated into existing Governance, Risk Management, and Compliance (GRC) platforms that support OSCAL. A visual representation demonstrates the automation opportunity machine-readable OSCAL artifacts provides.
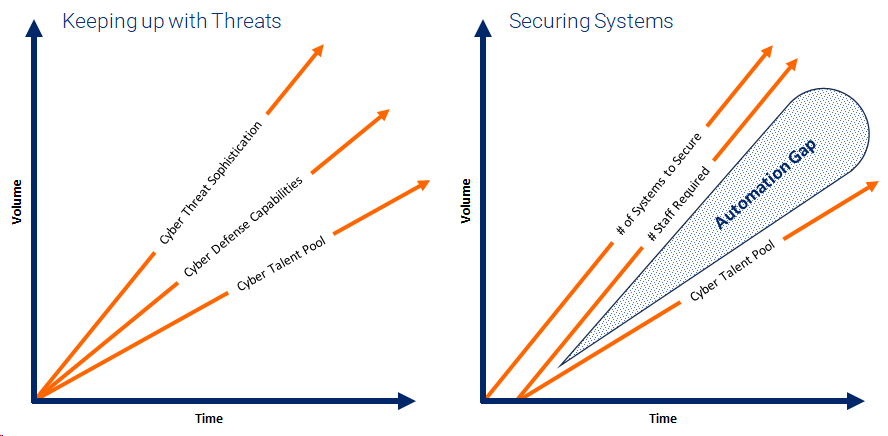
The Need for Automation in Cybersecurity As cyber threats become more sophisticated and cybersecurity talent remains scarce, relying solely on manual assessments is unsustainable. The growing complexity and volume of data and systems require scalable solutions. Automation and machine-driven assessments are not just beneficial; they are essential for expanding our regulatory oversight capabilities. The following figure provides a visual highlighting the automation opportunity necessary to address growing Cyber threat sophistication with a talent pool that can’t keep up (Graphic credit goes to Brian Ruf for this one).
Looking Forward: Regulatory Harmonization and Automation As we navigate the evolving landscape of cybersecurity threats, the integration of machine-driven assessments within the framework of continuous authorization is not merely advantageous—it is imperative. Leveraging OSCAL and automation will not only streamline our compliance processes but also enhance our nation’s defensive capabilities in a substantial way. I encourage my peers to explore these technologies and consider how they might be implemented within their own agencies. Together, we can transform the landscape of federal cybersecurity oversight for a safer, more resilient future.
